What is Next Generation Firewall?
Gartner proposed it in 2009. The next-generation firewall(NGFW) is an evolution of traditional firewalls (including traditional UTM). As network security protection becomes more and more complex and the security situation gradually deteriorates, traditional firewalls can no longer deal with new network threats. The birth of NGFW allows external network threats to be visualized, which can fully meet users' needs for network defense and management.
More robust application recognition capabilities, active defense against unknown threats, and the integration of multiple threat detection methods are the most significant features of NGFW that distinguish traditional network security equipment. It is a must as well for business in today's network environment.

- Multi-dimensional visibility and granular control improve daily business efficiency.
- L2-L7 layer comprehensive threat protection, 360° protection for your network.
- Strong network adaptability, rich deployment scenarios.
- Fully parallel hardware and software architecture, high-performance business experience.
Typical Applications of Next Generation Firewall
With intrusion prevention technology based on deep application, protocol detection, and attack principle analysis, FS NSG Series NGFW can effectively filter viruses, Trojan, worms, spyware, vulnerability attacks, escape attacks, and other security threats. It provides enterprises with L2-L7 layer network comprehensive security protection provides excellent security protection performance. The NSG series can be deployed in various industries such as government, finance, enterprise, education, etc. And it is widely used in multiple network application scenarios such as the edge of an enterprise network, servers protection, and branch VPN interconnection.
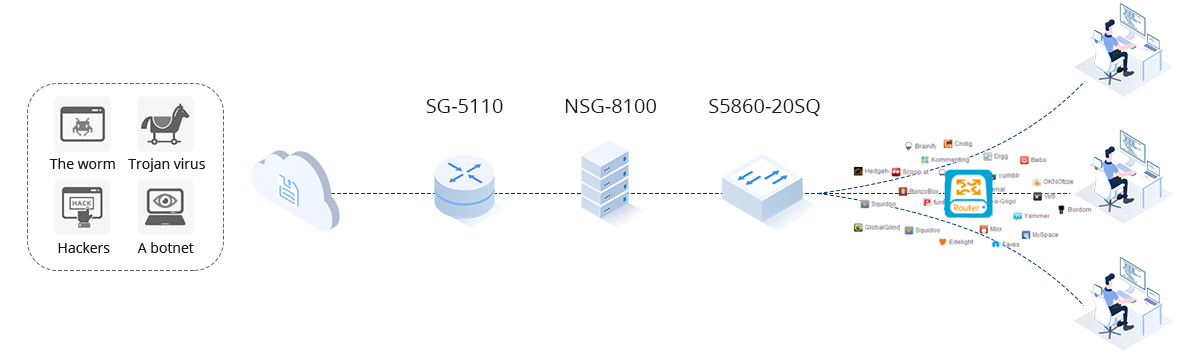
Edge Security of Enterprise Network
- High export bandwidth requires strong NAT performance.
- Lots of outgoing links, complicated outbound environment.
- Massive applications need to be released externally, occupying a lot of public IP.
- Need to guarantee the bandwidth of key businesses and services with limited bandwidth.
- The control of internet behavior is being challenged.Need to defend against Internet security threats effectively.
- High performance, scalable NAT/PAT technology.
- Professional link load balancing and application drainage technology.
- SmartDNS technology.
- Powerful application identification and rich traffic control strategies.
- Support real-name NAT logging and auditing.
- Comprehensive threat monitoring and defense.
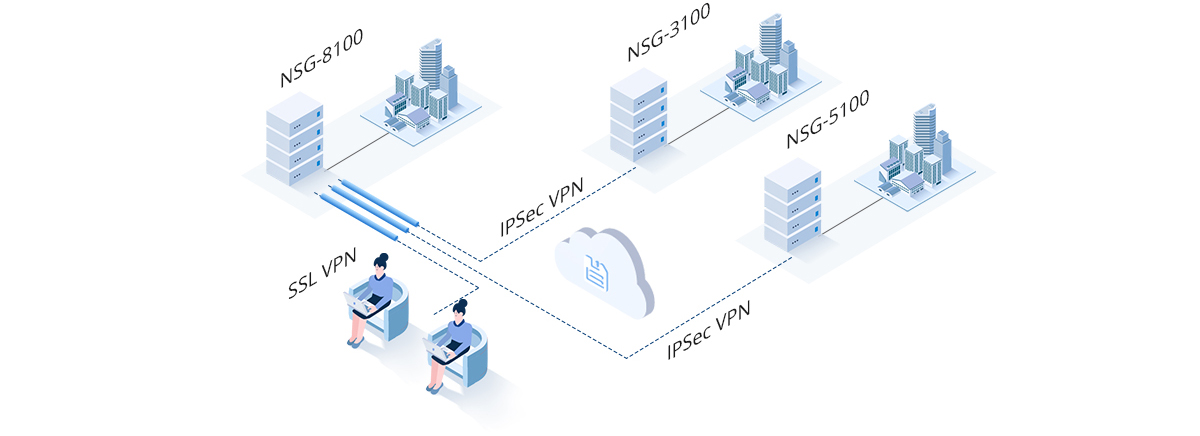
Branches VPN Interconnection
- Too many branches, resulting in low operation and maintenance
- capacity of most branches.
- No security guarantee for data transmission between branches and headquarters.
- Too many business travelers require remote access to their organizations' networks.
- Need to control the access permissions of users and occupied resources.
- Centralized deployment, monitoring, and management.
- Data encryption and verification to prevent data leakage.
- Rich VPN interconnection technologies to realize multi-scene interconnection.
- Access control based on employee identity.
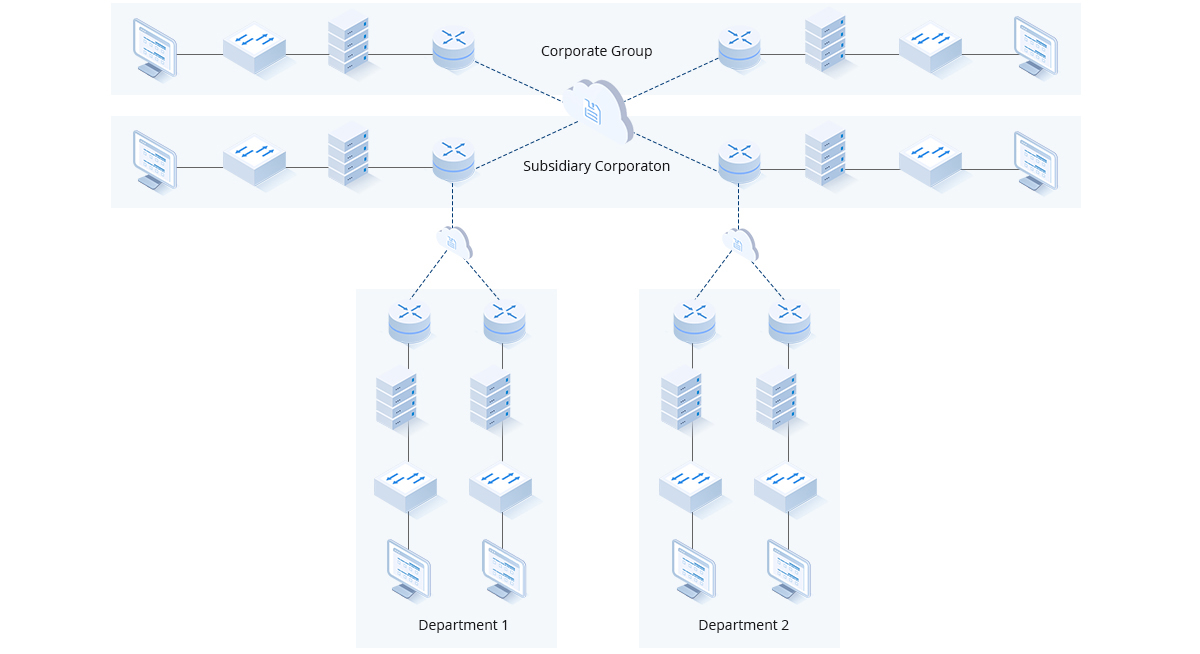
Intranet Isolation
- It is necessary to prevent unauthorized access and malicious attacks in the private network.
- Need to prevent intrusion attacks, virus infections, and other threats from other units.
- Need to control the access and log audit among users in the network.
- Perform flexible access control and intrusion detection and defense in the private network following the authority of all units.
- Smart threat detection and defense to prevent infiltration attacks, malicious programs, Trojan, virus and other threats from other units.
- Supports rich log functions, provides local log storage,and secure records leap to the eye.
Build Your OEM Solutions
Port | 5 x GE, 4 x Combo | 6 x GE, 4 x SFP | 4x GE, 4x SFP, 2x SFP+ |
Firewall Throughput | 2.5Gbps | 6Gbps | 10Gbps |
IPSec VPN Throughput | 1Gbps | 3Gbps | 6Gbps |
AV Throughput | 700Mbps | 1.2Gbps | 3Gbps |
IPS Throughput | 1Gbps | 1.8Gbps | 4Gbps |
NGFW Throughput | 650Mbps | 1Gbps | 3Gbps |
Threat Protection Throughput | 500Mbps | 800Mbps | 2Gbps |
New Sessions/sec | 50,000 | 80,000 | 170,000 |
Maximum Concurrent Sessions | 1M | 2M | 6M |
SSL VPN Users (Default/Max) | 8/1,000 | 8/2,000 | 8/8,000 |



